A search of Guidance Support Portal and I was able to down Winen.pdf. (Guidance Forum Access Required - 3 pages).
The Winen Executable can run as a command line tool, user prompt or from a configuration file. You can run Winen.exe from a USB drive that you plug into the Target Machine. You do need Local Administrator Privilege (which can be difficult to get- sometimes!).
If you can run Winen.exe from a USB Drive and it will prompt you for the required information needed to create the image file.
If you set up a configuration (Config) file you can speed things up.
Setting Up a Configuration File.
I created the following Config File:

As you can see I really placed the name of the image(Evidence Name)in the Evidence Path. In the Evidence Name Path I also put in the Evidence Name. This is so when I run the program it will automatically save my image file to the USB Device I am running it from.
In my example I will create a RAM_ACQ.e01 file in the same directory as I have Winen.exe installed on.
Batch File
I then created a batch file with the following line:
winen -f winen.config
“winen” is the executable to run
“-f” is the option for a Config File
“winen.config” is the name of my Config File (Must be in same path as Winen.exe)
Run the Batch file from your USB and you will automatically save you image file to your USB Drive.
Final Tweak
You can also change the name of winen.exe to something benign sounding (e.g. “sys32.exe”) to make it more difficult to identify by your target.
Using your RAM Acquisition e01 File.
Once the RAM image is created you can get information out of it by Using my RAM Enscript.
You can also use PtfinderFE on the RAM Image but you have to strip the embedded e01 data from your image file. My favorite way is by opening the image up in FTK Imager and export the unallocated space out. You could do the same thing in Encase.
 FootPrint
FootPrintWinen.exe will use approximately 2.8 Mb of RAM which might also be found in the PageFile.
The following keys will be created or altered:
HKEY_LOCAL_MACHINE\SYSTEM\
HKEY_LOCAL_MACHINE\SYSTEM\
(Acording to the Winen.pdf)
Changes regarding adding a USB would also apply (e.g. USBStor in the Registry).
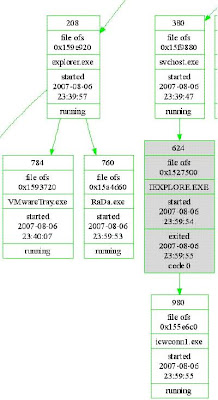
The batch file(cmd.exe) and Winen.exe (in the picture) as they appear in a PtfinderFE Graphic.
KntTools is still my RAM Acquisition tool of choice.