exemplar6.tar.gz.001
exemplar6.tar.gz.002
exemplar6.tar.gz.003
In my example I placed the files in e:\exemlar6\ directory
2. Add the downloaded files together and extract with the following cmd prompt code:
Copy /b “exemplar6.tar.gz.001”+ “exemplar6.tar.gz.002”+” exemplar6.tar.gz.003” exemplar6.tar.gz
3. Extract using WinRAR (exemplar6.tar.gz to exemplar6.vmem)
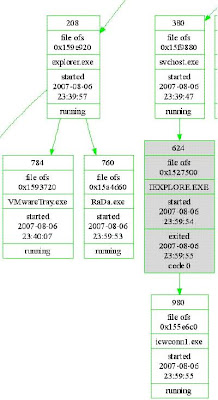
4. Run PtfinderFE against extracted file(exemplar6.vmem) which creates exemplar6.txt

5.Run Volatility Batch File Maker.
-a. Select e:\exemlar6\xemplar6.vmem with “Browse for Memory Capture”.
-b. Select e:\exemlar6\exemplar6.txt (created by PtFinderFE) for your memory image with “Browse for Offset Text File”.
-c. Create Batch (Which is hidden until the previous listed fields are populated).
6. .Goto the directory containing exemplar6.vmem (e:\exemlar6\) and run e:\exemlar6\procdump.bat file.
7.Browse the e:\exemlar6\procdump folder.

8.Use an anti-virus tool against the reconstructed executable files in the e:\exemlar6\procdump directory
I decided to send the files to Virus Total for testing. Using their "Send to" Function.
PID 464 - “dw8.exe”(Virus Total Results: 13 of 40 Hits)
PID 648 ”tdctxte.exe” (Virus Total Results: 116 of 41 Hits)
PID 872 ”atsxyzd.sys” (Virus Total Results: 117 of 41 Hits)
PID 1056 ”dxonool32.sys” (Virus Total Results: 119 of 40 Hits)
PID 1876 ”sopidkc.exe” (Virus Total Results: 14 of 41 Hits)
PID 1932 ”afisicx.exe” (Virus Total Results: 119 of 40 Hits)
Some Additional Notes and Some Background:
I'm not sure why but it seems the executables that have unique icons instead of the generic executable icons have a high percentage of being malicious.
Until I created Volatility Batch File Maker I was using batch file, and changing input via a spreadsheet and some “find and replace” functions. One of the batch file I created attempted to use ProcDump on all the PIDs (-p option) from 0 to 6000. Reconstructed executables were only made for PIDs that were listed as running by Ptfinder. I also tried using Procdump offset (-o option) function with the same results(and ALOT more time!!!).
I was analyzing a “real world” machine which was running over 90 processes. I placed the executables created by ProcDump into a zip files, by groups of 10. I then sent them up to Virus Total for Scanning. Unfortunately when I found a hit there was no way to determine which file out of the group of ten was the suspected malware file.
I would like to start an ssdeep database of common executables created by Procdump.