You must download the RADA Virus if you want to “play” along. The RADA Virus is a REAL VIRUS SO BE CAREFUL…
The RADA VIRUS was created several years ago to test other geeks participating in the HONEYNET Project. Also download one of the best solutions to the RADA Challenge (But don’t read the solution, yet…).
Make three folders in you working directory called: Baseline, Infected and Start_and_Stop. Start your machine (After you clone your pristine VMWARE Win2000 Machine). When you machine completely boots suspend your machine. Another term often used for suspend is “pause” because the VMWARE “Suspend” Button looks just like a regular “Pause” button. . Copy the VMEM file from you VM Directory into your working directory titled” Baseline”.
In my example I am copying the VMEM file from my VMWARE Machine Called Win2000-Rada.VMEM to the working “Baseline” Folder.

Now Resume the machine and add the RADA Virus. I choose to originally copy the virus to a CD so I place the CD in the machine and copy RADA to a Folder called "Virus" on my Desktop.

Now double click on RADA. Wait a second and “Suspend” the machine.
If you did not run the Connection Wizard prior to infection you will probably see the following:

Copy the VMEM file to you “Infected” Folder. Resume your machine. Using your machine’s own functions restart the machine. Once the machine reboots suspend the machine again and copy the VMEM file to the Stop_and_Start Folder.
So now we have 3 VMEM files copied into our three working folders.
Run PTFinder or PTFinderFE against the “baseline” VMEM and review the chart.
Now run PTFinder or PTFinderFE against the “Infected” VMEM and review you chart. You should see something like the following:
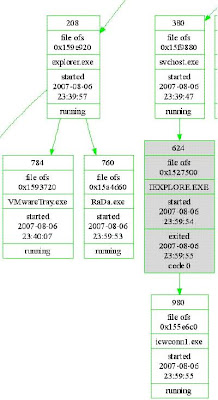
In our example the Offset of RADA= 0x15a4d60
To make my life easier I just copy cmd.exe, lspm.exe and p2x588.dll (needed by lspm.exe to run) into my “Infected” working directory. Run cmd.exe which opens to your working folder and type the following:
lspm Win2000-Rada 0x15a4d60 (and Enter)

Rada.dmp is created and put in the “Infected” Working Folder. Rada.dmp is a copy of the RADA.Exe Program as copied out of volatile memory.
Open Rada.dmp with AnalogX’s TextScan and look for important information. The following is a truncated sample of the text taken from my exam.
72457 Unichar 42 http://10.10.10.10/RaDa/RaDa_commands.html
75214 Unichar 20 C:\RaDa\bin\RaDa.exe
95754 Unichar 42 http://10.10.10.10/RaDa/RaDa_commands.html
102470 Unichar 55 HKLM\Software\Microsoft\Windows\CurrentVersion\Run\RaDa
103114 Unichar 27 C:\WINNT\System32\wshom.ocx
105509 Unichar 49 C:\Program Files\Internet Explorer\iexplore.exe
112221 Unichar 29 pec=C:\WINNT\system32\cmd.exe
122742 Unichar 42 http://10.10.10.10/RaDa/RaDa_commands.html
188853 Char 40 !This program is the binary of SotM 32..
197922 Unichar 23 http://10.10.10.10/RaDa
197974 Unichar 18 RaDa_commands.html
198038 Unichar 12 download.cgi
198070 Unichar 10 upload.cgi
198098 Unichar 11 C:\RaDa\tmp
198150 Unichar 51 HKLM\Software\Microsoft\Windows\CurrentVersion\Run\
198294 Unichar 11 C:\RaDa\bin
198346 Unichar 51 HKLM\Software\VMware Inc.\VMware Tools\InstallPath
198454 Unichar 36 Starting DDoS Smurf remote attack...
198611 Char 15 Command_install
198643 Char 53 You can learn a lot playing funny security challenges
198747 Char 13 Command_usage
198763 Char 12 Command_exit
198779 Char 12 Command_conf
198835 Char 10 Command_go
198847 Char 17 Command_uninstall
199577 Unichar 15 http://192.168.
199613 Unichar 14 http://172.16.
199649 Unichar 10 http://10.
199685 Unichar 28 InternetExplorer.Application
199813 Unichar 11 about:blank
199985 Unichar 10 screenshot
200026 Unichar 11 Application
200096 Unichar 44 Scan Of The Month 32 (SotM) - September 2004
200240 Unichar 40 http://www.honeynet.org/scans/index.html
200328 Unichar 43 Copyright (C) 2004 Raul Siles & David Perez
200420 Unichar 25
200885 Unichar 41
201145 Unichar 38 "Content-Disposition: form-data; name="""
201257 Unichar 11 Submit Form
201297 Unichar 44 Content-Type: multipart/form-data; boundary=
201442 Unichar 18 application/upload
201486 Unichar 15 ADODB.Recordset
201634 Unichar 47 "Content-Disposition: form-data; name=""{field}"";"
201734 Unichar 18 " filename=""{file}"""
201778 Unichar 18 Content-Type: {ct}
202062 Unichar 50 Copyright (C) 2001 Antonin Foller PSTRUH Software
203147 Unichar 39 Authors: Raul Siles & David Perez 2004
Wow there is a lot of information in the little DMP File. Now go look at the Solution you downloaded. Our 15 minutes of research is not too shabby.
No comments:
Post a Comment